
Introduction: What is glue and tap fraud?
Glue and tap fraud is a scam where criminals sabotage an ATM by filling the card reader slot with glue, forcing the victim to use the “Tap”feature. After the victim completes their transaction, they might forget to select the “finished” option on the screen, leaving their session open. This oversight allows the criminal to withdraw money from the victim’s account.
The Problem: How is it different than other forms of fraud? Why is it a growing cause for concern?
Glue and tap fraud stands out from other types of fraud primarily because it is a sophisticated form of social engineering. Unlike traditional fraud, which often relies on technology or brute force to exploit vulnerabilities, this method manipulates human behavior. Criminals involved in glue and tap fraud usually pose as helpful bystanders. They might approach the victim under the guise of helping when the card reader appears to be malfunctioning. By doing so, they subtly encourage the victim to use the “Tap” function, making the victim believe that it is the only viable option to complete their transaction.
This type of fraud is particularly concerning because it preys on the trust and helpfulness of individuals, making it more difficult for victims to recognize the scam.Additionally, as more ATMs and payment terminals adopt contactless technology, the potential for this kind of fraud is increasing. The growing prevalence of this scheme makes it a significant threat, as it combines both psychological manipulation and technical interference, leading to substantial financial losses for unsuspecting victims.
Furthermore, the reliance on human interaction in this fraud makes it harder to detect and prevent through conventional security measures, thus posing a growing challenge for banks and financial institutions to protect their customers.
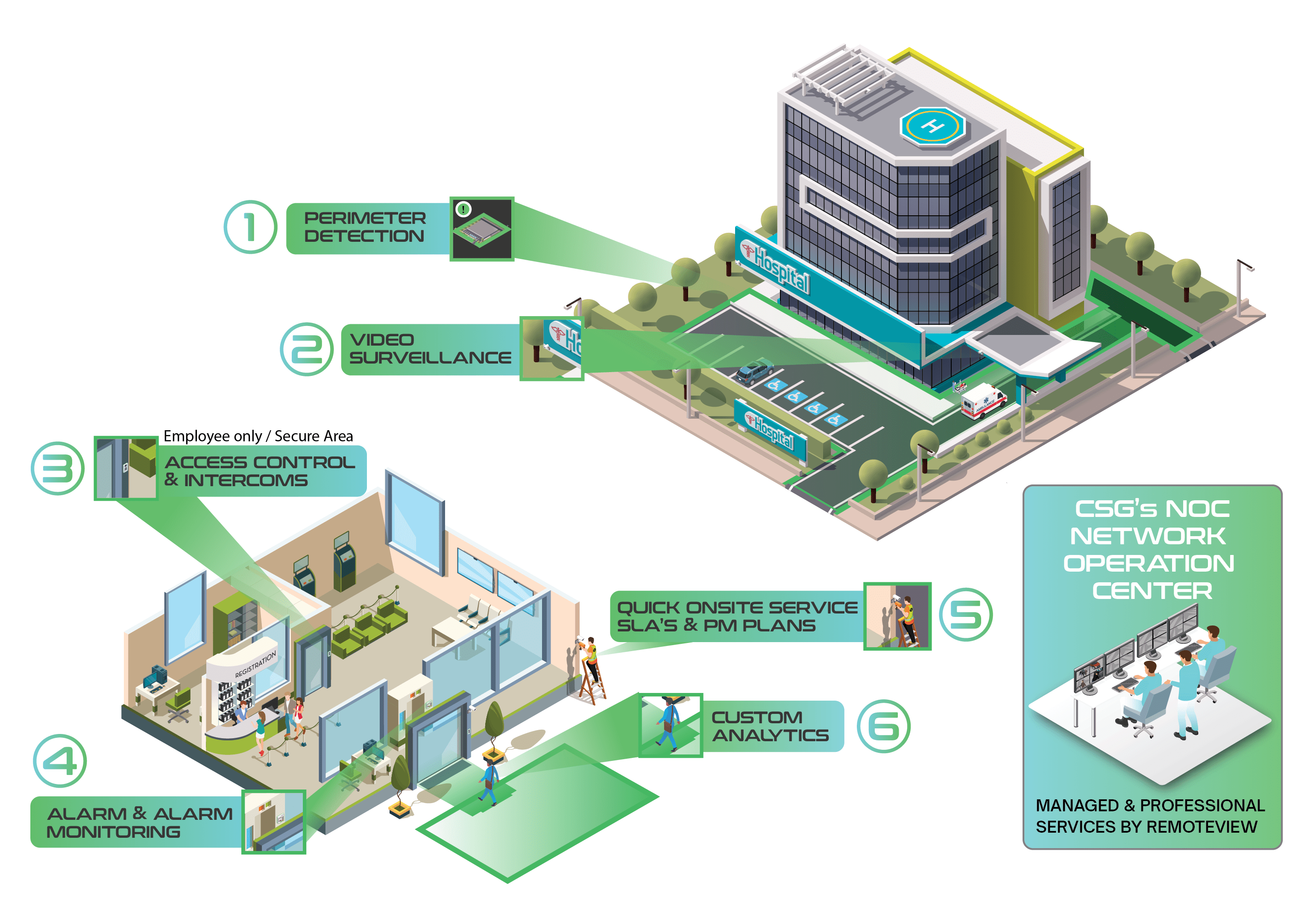
The solution: What steps can I take to protect my machine and cardholders?
To combat this type of ATM social engineering attack, it is essential to educate your cardholders on recognizing and reporting any suspicious behavior near your ATMs. Awareness is a key defense in preventing these scams.
Beyond cardholder education, Cook Solutions Group offers a range of security solutions designed to protect ATMs from such attacks. Our integrated, layered approach combines AI surveillance, transaction validation, and screen recording, creating a robust defense against both physical and digital threats. Learn more about how we can help by contacting us below!
References:
ATM scammers use 'glue and tap' to steal funds . (n.d.). Retrieved from ATM Marketplace: https://www.atmmarketplace.com/news/atm-scammers-use-glue-and-tap-to-steal-funds/#:~:text=In%20the%20scam%20a%20criminal,they%20use%20the%20tap%20feature.
Koury, R. (2023, March 10). More Chase customers lose money to ATM thieves using glue and 'tap' feature to steal . Retrieved from ABC7 News: https://abc7news.com/glue-in-atm-slot-chase-scam-tap-card-bank/12935385/
Man goes undercover to prove Chase bank ATM glue and tap scam. (n.d.). Retrieved from ATM Marketplace: https://www.atmmarketplace.com/news/man-goes-undercover-to-prove-chase-bank-atm-glue-and-tap-scam/
CSG's unique approach against multiple types of ATM fraud.
Our strategy extends beyond traditional surveillance, incorporating real-time monitoring, intelligent analytics, and proactive threat detection. Our approach is based on a layered security strategy that addresses various vulnerabilities, including:
- Hook & Chain, Physical Attacks: Fortify terminals against brute force attacks aiming to extract cash.
- Reg E Claims: Support compliance with Regulation E by providing evidence and transaction verification to resolve disputes.
- Software Vulnerabilities: Utilize AI based Endpoint Security to shield the ATM operating system from malware and other cyber threats.
- Data Compliance: Ensure the confidentiality and integrity of data stored on terminal hard drives using hard drive encryption.
- Card Skimming, Deep Insert and Cash Harvesting: Prevent unauthorized data capture and cash removal from terminals.
- Terminal Jackpotting: Guard against unauthorized software manipulation aiming to dispense cash fraudulently.
- Cash Dispensing and Cash Trapping: Secure dispensing mechanisms from tampering and unauthorized cash trapping devices.
- Transaction Reversal Fraud (TRF): Protect against manipulation techniques that reverse transactions to withdraw cash.
- Man-in-the-Middle (MITM) Attacks: By placing a device between the ATM and the Host, attackers pursue objectives such as interception, eavesdropping, modification, and impersonation.


































.png)







