What is jackpotting?
According to the U.S Attorney’s Office, jackpotting is defined as a “type of cyberattack where criminals exploit vulnerabilities in ATMs to force them to dispense cash without debiting an account”. This type of fraud does not impact cardholders but instead, it directly impacts the financial institution. Lately the trend with jackpotting has been what we call a “hard drive attack”. These specific types of attacks happen by one or more individuals that gain access to the top of the ATM where the PC is located. These attacks are often conducted by large criminal organizations and are a coordinated effort among many people. Before the attack is ever conducted, the attackers will surveil the area beforehand. Often taking pictures of the machine to determine eligibility.

Opening the top of the machine is usually done by prying it open or by using a key that can be purchased online. Once they gain access the PC itself is pried or cut open, and the hard drive is removed. Once the hard drive has been removed the individual(s) inject malware onto the hard drive while it is removed from the PC. Sometime later (hours or days) they will return to the location and replace the compromised drive into the machine to conduct their attack. During the attack they are sending commands and telling the machine to empty the cassettes without ever swiping a card or entering a PIN. Occasionally, a phone or mobile hotspot is used to facilitate a remote internet connection to the machine—avoiding firewall or network detection. This type of attack leaves ALL manufacturers of ATMs vulnerable.
As the digital landscape continues to evolve, so do the methods employed by criminals seeking illicit gains. In 2018, the U.S. Secret Service sounded the alarm on a burgeoning threat – jackpotting attacks. Defined as a sophisticated form of criminal activity, jackpotting involves the installation of malicious software and/or hardware at Automated Teller Machines (ATMs), compelling these financial terminals to dispense substantial amounts of cash at the whims of criminals. We delve into the intricacies of logical jackpotting attacks, shedding light on the methods perpetrators employ to gain physical access to ATMs, manipulate their operations with malware and/or specialized electronics, and exploit vulnerabilities in the system. Furthermore, it outlines practical steps and cutting-edge solutions CSG offers, such as rekeying ATMs, implementing SAN Loitering technology, and adopting the CSG Security + solution which uses CylancePROTECT from Blackberry, aimed at mitigating the risk posed by this sophisticated and evolving form of financial cybercrime.
How does it happen?
Per the definition above, two things must take place for a logical malware based jackpotting attack to occur. The first thing needed by a perpetrator is physical access to the machine. Physical access is easy to obtain with a quick search on the internet for a “universal ATM key”. These can be ordered on Amazon, eBay, and many other online platforms. Once physical access has been obtained, the criminal(s) will install malware on the machine via an open port (USB orEthernet). This malware takes advantage of the software on the ATM and tells the machine to dispense all the cash in the cassettes. This is not tied to a card or any specific account. Other forms of jackpotting attacks include a man in the middle attack and black box attacks.
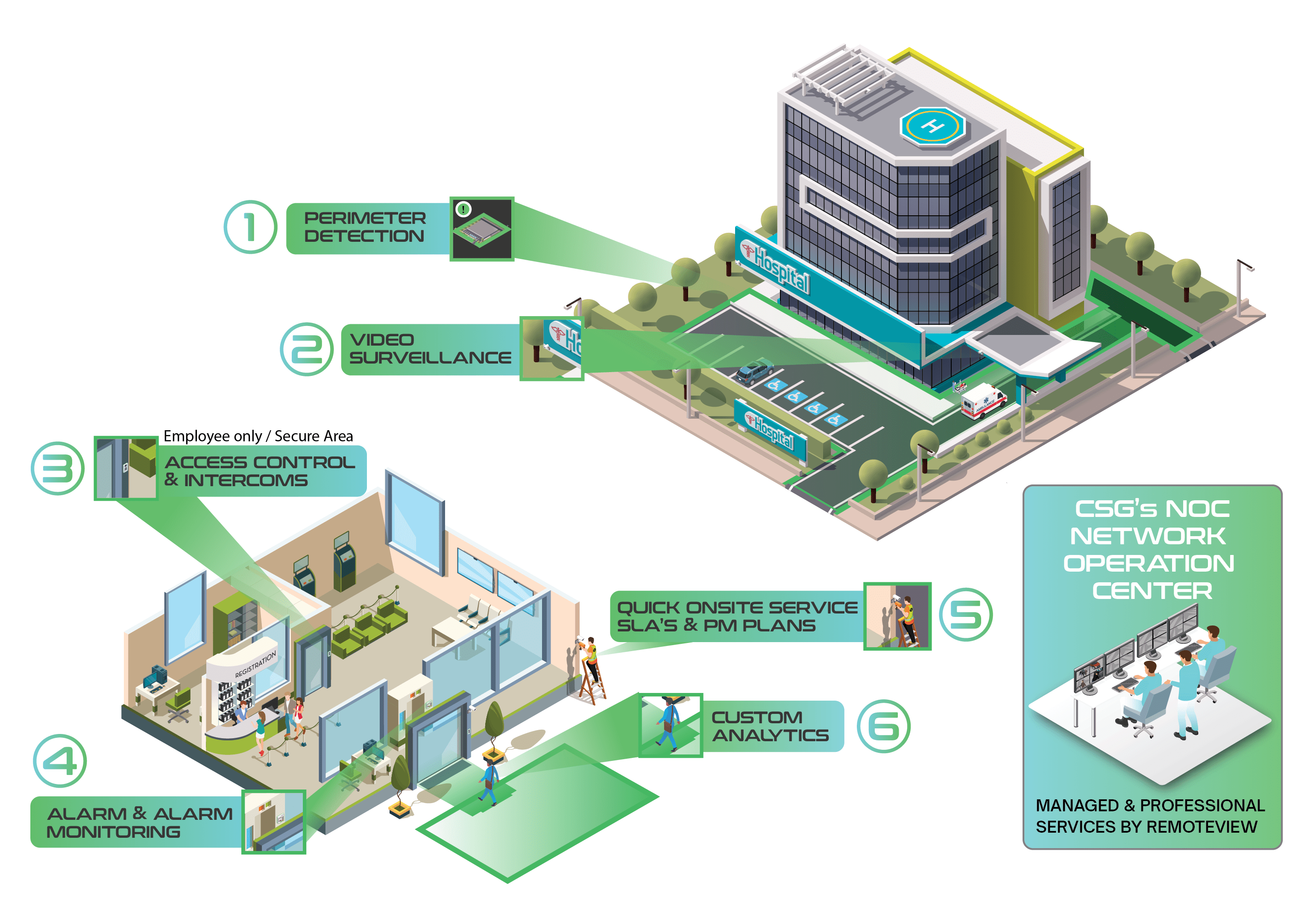
CSG's unique approach against multiple types of ATM fraud.
Our strategy extends beyond traditional surveillance, incorporating real-time monitoring, intelligent analytics, and proactive threat detection. Our approach is based on a layered security strategy that addresses various vulnerabilities, including:
- Hook & Chain, Physical Attacks: Fortify terminals against brute force attacks aiming to extract cash.
- Reg E Claims: Support compliance with Regulation E by providing evidence and transaction verification to resolve disputes.
- Software Vulnerabilities: Utilize AI based Endpoint Security to shield the ATM operating system from malware and other cyber threats.
- Data Compliance: Ensure the confidentiality and integrity of data stored on terminal hard drives using hard drive encryption.
- Card Skimming, Deep Insert and Cash Harvesting: Prevent unauthorized data capture and cash removal from terminals.
- Terminal Jackpotting: Guard against unauthorized software manipulation aiming to dispense cash fraudulently.
- Cash Dispensing and Cash Trapping: Secure dispensing mechanisms from tampering and unauthorized cash trapping devices.
- Transaction Reversal Fraud (TRF): Protect against manipulation techniques that reverse transactions to withdraw cash.
- Man-in-the-Middle (MITM) Attacks: By placing a device between the ATM and the Host, attackers pursue objectives such as interception, eavesdropping, modification, and impersonation.
View ATM Terminal Security solutions & video
References:
Cook Solutions Group. (n.d.). Application Control & Patch Management. Retrieved from Cook Solutions Group: https://www.cooksolutionsgroup.com/managed-services/security-modules-patch-management
Cook Solutions Group. (n.d.). Cook Solutions Group. Retrieved from ATM Fraud Deterrents: https://www.cooksolutionsgroup.com/security-solutions/atm-itm-skimming-attacks-deterrents
Lott, D. (2022, March 21). ATM Jackpotting Attacks Getting Clever. Retrieved from Federal Reserve Bank of Atlanta: https://www.atlantafed.org/blogs/take-on-payments/2022/03/21/atm-jackpotting-attacks-getting-clever







































.png)








