Abstract:
This article explores the threat landscape of Man-in-the-Middle (MITM) attacks on ATMs and ITMs, shedding light on the methods and goals of attackers. By placing a device between the ATM and the Host, attackers pursue objectives such as interception, eavesdropping, modification, and impersonation. A detailed example of a physical black-box attack involving a Raspberry PI and USB to Ethernet adapters is presented.
The article discusses the diverse means by which MITM attacks can occur, ranging from physical access to lateral movement through a Financial Institution's network facilitated by email phishing. Practical solutions to mitigate risks are provided, encompassing user training, network segmentation, and security measures like concealing cables and employing MAC address filtering.
Additionally, the article highlights cybersecurity solutions offered by CSG, including the RemoteView product with quarterly patches and the Security+ module, along with Smart Camera Analytics for real-time surveillance and rapid response to potential threats. Understanding and implementing these measures are imperative in safeguarding financial systems against evolving cyber threats.

Introduction: What is a Man-in-the-Middle (MITM) attack?
A Man-in-the-Middle(MITM) occurs by placing a device between the ATM and the Host. There are two methods for MITM attacks. The attacker can gain access via malware or via a “blackbox”. There are four main goals for MITM attacks: Interception, Eavesdropping, Modification, and/or Impersonation. In the picture below you can see an example of what one of these Black-Box attacks look like:

In this example, the attacker used a Raspberry PI that was preprogrammed with malicious code and USB to Ethernet adapters to intercept communications between the ATM and the Network.
The Problem: How does it happen?
For a MITM black-box attack to take place, the attacker must first access the LAN network cable via the top hat of the ATM or the network jack in the wall. Once they have access, the attacker plugs in their device “in-line” with the existing connection. The attacker may also opt for connecting directly to the cash dispenser in the machine and send commands directly to the dispenser to empty its cassettes.
As mentioned earlier, not all MITM attacks require physical access to an ATM these days. Another way this can be accomplished is via lateral movement through a Financial Institutions network. Email Phishing is the most common way network access is obtained.

( H 4 c k s p l o i t , 2 0 2 3 )
The Solution: What steps can I take to mitigate my risk?
To ensure that your network and ATMs are secure, there are several things your Financial Institution can do today.
- Train all end users on phishing, smishing, and other similar attacks and how to properly spot and report them.
- from a networking perspective, ensure that your ATMs are segmented off from the rest of your network. This will make it much harder for attackers to gain access to your machines.
- Protect your network by ensuring that all network cables are hidden from view. Consider employing MAC address filtering across your network if it is not already. This will ensure that only authorized devices can access your network.
In addition to these immediate solutions, CSG offers several solutions that directly relate to mitigation of MITM attacks. Here are a couple of highlights:
- All ATMs on CSG’s RemoteView product areprotected with quarterly windows patches and our Security+ module. Security+uses Blackberry’s Cylance PROTECT to lock down all peripheral device access and protection from zero-day attacks.
- CSG’s Smart Camera Analytics provide real-time notifications with surveillance footage to detect loitering, vandalism, and fraud. In addition to the real-time notifications our Managed Services team can remotely take your ATM out of service or shut it down to stop an attack in its tracks.
References:
Amado, J. (2020, July 14). Sepio Cyber. Retrieved from Black Box Attack : https://sepiocyber.com/blog/atm-black-box-attacks/
Cook Solutions Group. (n.d.). Application Control & Patch Management. Retrieved from Cook Solutions Group: https://www.cooksolutionsgroup.com/managed-services/security-modules-patch-management
Cook Solutions Group. (n.d.). How much time does your IT staff spend to support your security and ATM/ITM infrastructure? Retrieved from Cook Solutions Group: https://www.cooksolutionsgroup.com/managed-services-new/network-operations-center
Gemert, W. v. (n.d.). NCR. Retrieved from EuroPol_Guidance-Recommendations-ATM-logical-attacks: https://www.ncr.com/content/dam/ncrcom/content-type/brochures/EuroPol_Guidance-Recommendations-ATM-logical-attacks.pdf
H4cksploit. (2023, May 8). Hacking Atms Using Black Box. ATMJackpotting. Retrieved from Medium: https://h4cksploit.medium.com/hacking-atms-using-black-box-atmjackpotting-dd3056abcc9e
Minin, R. (2021, January 25). Man in the Middle Attack . Retrieved from Sepio Cyber: https://sepiocyber.com/blog/man-in-the-middle-attack/
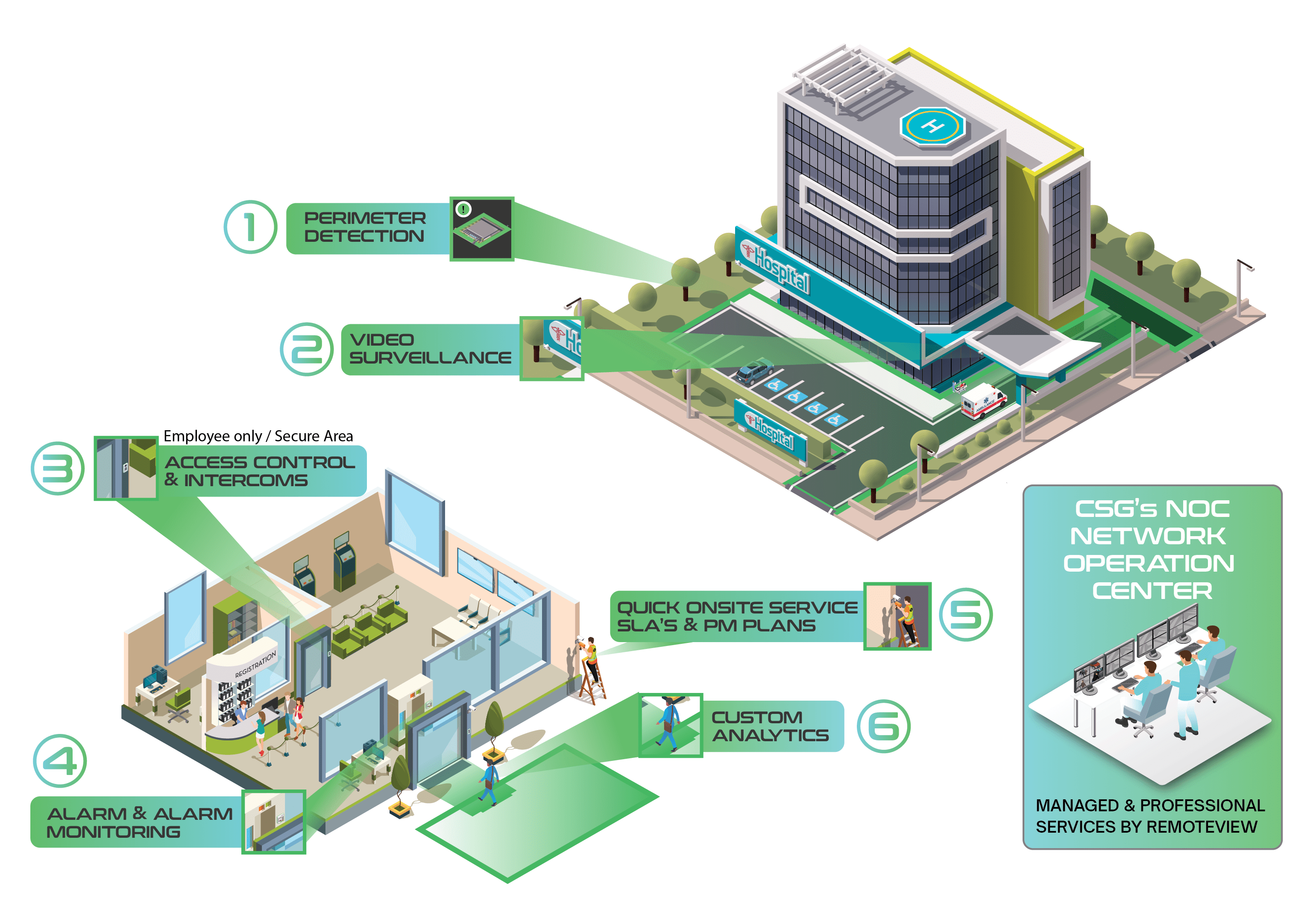
CSG's unique approach against multiple types of ATM fraud.
Our strategy extends beyond traditional surveillance, incorporating real-time monitoring, intelligent analytics, and proactive threat detection. Our approach is based on a layered security strategy that addresses various vulnerabilities, including:
- Hook & Chain, Physical Attacks: Fortify terminals against brute force attacks aiming to extract cash.
- Reg E Claims: Support compliance with Regulation E by providing evidence and transaction verification to resolve disputes.
- Software Vulnerabilities: Utilize AI based Endpoint Security to shield the ATM operating system from malware and other cyber threats.
- Data Compliance: Ensure the confidentiality and integrity of data stored on terminal hard drives using hard drive encryption.
- Card Skimming, Deep Insert and Cash Harvesting: Prevent unauthorized data capture and cash removal from terminals.
- Terminal Jackpotting: Guard against unauthorized software manipulation aiming to dispense cash fraudulently.
- Cash Dispensing and Cash Trapping: Secure dispensing mechanisms from tampering and unauthorized cash trapping devices.
- Transaction Reversal Fraud (TRF): Protect against manipulation techniques that reverse transactions to withdraw cash.
- Man-in-the-Middle (MITM) Attacks: By placing a device between the ATM and the Host, attackers pursue objectives such as interception, eavesdropping, modification, and impersonation.