How to detect and protect against ATM Fraud and Attacks?
View ATM Terminal Security solutions & video
Hook & Chain ATM / ITM Attack Update
What is a Hook and Chain ATM attack?
A hook and chain ATM attack is a type of criminal activity targeted at automated teller machines (ATMs). In this method, criminals typically operate between 11 p.m. and 6 a.m. when there are fewer people around. The attack involves attaching one end of a chain or cable to an ATM and using a vehicle to exert force on the machine, usually by pulling the chain with the vehicle. The objective is to forcefully open the ATM's safe doors, allowing the criminals to access the cash inside.
These attacks can cause significant property damage and financial losses. To prevent hook and chain ATM attacks, various strategies and security measures are deployed, such as installing anti-ramming bollards, using reinforced ATM enclosures, and enhancing surveillance in ATM locations.
This information is based on various sources, including articles on ATM security strategies and solutions to prevent such attacks, as well as an overview of the modus operandi of hook and chain ATM attacks.
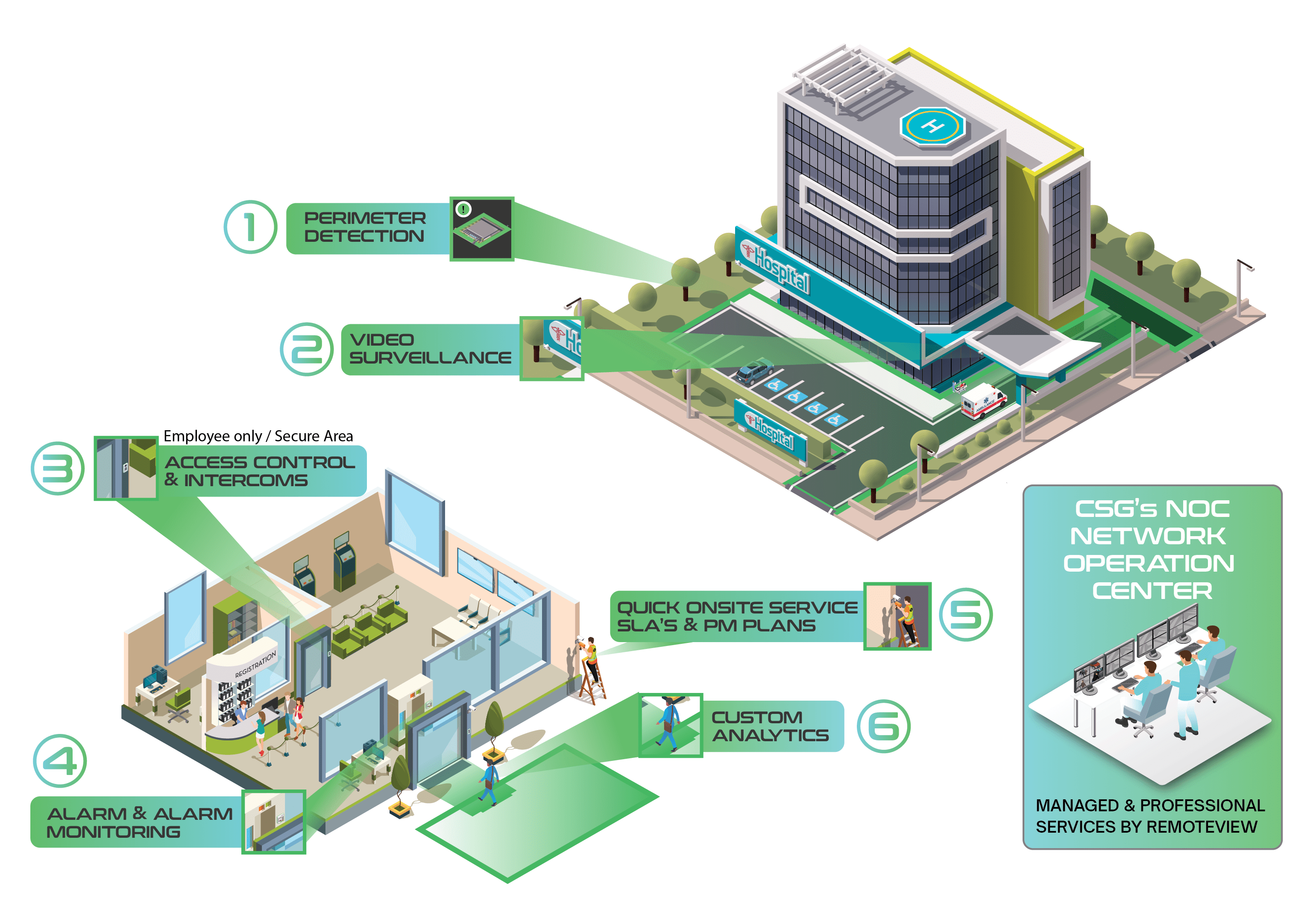
Cook Solutions Group constructed the Cook Command Center to provide customers a fully interactive platform enabling users with a comprehensive view of their current products and equipment. Whether it be requesting service or viewing transactional data the Cook Command Center allows our customers the ability to view, manage and interact with their current line of Cook Solutions Group products.
- Access service history, preventative maintenance & survey information
- View Real-Time Status and Electronic Journals with RemoteView ATM
- Easily request service for all hardware and equipment
- Case Management makes it easy to share information and files with internal/external parties.
Command Center is strategically broken out into different platforms each providing customers unique viewpoints into their infrastructure: CustomerView, RemoteView and System.
Hook & Chain ATM / ITM attacks and resulting losses have skyrocketed in the Western U.S. over the last year.
Other ATM threats
- What is an ATM Skimming attack? An ATM skimming attack is a form of payment card fraud where criminals install illicit devices, known as "skimmers," on ATM machines or point-of-sale terminals. These skimmers are designed to secretly capture the data from the magnetic stripe of debit or credit cards when unsuspecting individuals use the compromised machine. The stolen card information is then used to make unauthorized transactions or create cloned cards, leading to financial losses for the victims. ATM skimming attacks are often challenging to detect, as the devices are typically discreetly attached, and the fraudulent activity may go unnoticed for extended periods, sometimes weeks or even months.
- What is an ATM Deep Insert Skimmer? An ATM Deep Insert Skimmer is a high-tech illegal tool that steals cardholder info and money from ATM users. These skimmers are designed to be placed deep inside the ATM card slot. As a result, they are difficult for both users and ATM operators to detect.
- What is ATM Jackpotting? The process typically involves criminals gaining physical access to an ATM, either by tampering with its components or using specialized tools and techniques to access its internal systems. Once inside, they execute commands that instruct the ATM to dispense cash continuously until it is empty. ATM jackpotting attacks have become more sophisticated over time, with criminals continually evolving their techniques to bypass security measures and maximize their gains.
- What is Object Detection? Object detection is a tech that finds and locates objects in images and videos using computer vision and image processing. In relation to ATM attacks, it can be used to identify Trucks, Heavy Equipment, tools and other attack supplies.
- Learn how Piko Video Surveillance Analytics leverages AI and machine learning to catch criminals.
In our webinar you will learn how to combat or deter these physical ATM attacks, plus:
- Piko Unified Securiy Platform Deterrent Technology
- How and when are these attacks occurring
- Strategies for performing attack risk assessments on your institutions ATM/ITM fleet
- Layered security solutions available to reduce the risk of attack
- Strategies for utilizing communication and technology to increase the speed and effectiveness of response if an attack occurs
In case you missed CSG’s ATM/ITM Hook & Chain Threats and how to prevent them, you can request a copy or book a private meeting with our security experts below.
CSG's unique approach against multiple types of ATM fraud.
Our strategy extends beyond traditional surveillance, incorporating real-time monitoring, intelligent analytics, and proactive threat detection. Our approach is based on a layered security strategy that addresses various vulnerabilities, including:
- Hook & Chain, Physical Attacks: Fortify terminals against brute force attacks aiming to extract cash.
- Reg E Claims: Support compliance with Regulation E by providing evidence and transaction verification to resolve disputes.
- Software Vulnerabilities: Utilize AI based Endpoint Security to shield the ATM operating system from malware and other cyber threats.
- Data Compliance: Ensure the confidentiality and integrity of data stored on terminal hard drives using hard drive encryption.
- Card Skimming, Deep Insert and Cash Harvesting: Prevent unauthorized data capture and cash removal from terminals.
- Terminal Jackpotting: Guard against unauthorized software manipulation aiming to dispense cash fraudulently.
- Cash Dispensing and Cash Trapping: Secure dispensing mechanisms from tampering and unauthorized cash trapping devices.
- Transaction Reversal Fraud (TRF): Protect against manipulation techniques that reverse transactions to withdraw cash.
- Man-in-the-Middle (MITM) Attacks: By placing a device between the ATM and the Host, attackers pursue objectives such as interception, eavesdropping, modification, and impersonation.



































.png)





