How to detect and protect against ATM Fraud and Attacks?
View ATM Terminal Security solutions & video

What is deep insert skimming?
Deep insert skimmers are wafer thin fraud devices that are incredibly difficult to detect. These skimming devices have been reported to be found on all ATM manufactures in many countries including the United States. These skimmers are hidden from view and placed inside of the card reader. Deep insert skimmers are designed to read the magnetic stripe track 2 data which contains all card information in plain text and stored on a small memory chip. To successfully steal a cards data, the criminals also need to obtain the PIN. The PIN is commonly obtained by hidden cameras placed on the fascia near the PIN pad.

The Problem: How is it different than other forms of skimming? Why is it a growing cause for concern?
Deep insert skimming is different than other types of skimmers due to the skimmer being completely hidden inside of the card reader. Due to the incredibly low profile of these deep insert skimmers, they are not detected by most anti-skimming jamming and fraudulent device detections.
The Solution: What steps can I take to protect my machine?
To protect your machines, one of the first things your institution can do, is deny all magnetic stripe (fallback) transactions. Doing this will ensure that EMV chip transactions are the only authorized transactions by your ATM host network. EMV transactions create unique tokens that cannot be reused if skimmed. PIN pad covers are another measure you can take to protect your card holders PIN from being captured by a hidden camera. In addition to these two solutions, Cook Solutions Group offers a multi layered approach to protection by way of our Suspicious Activity Notification that can both alert and prevent skimming. In 2023, this technology resulted in dozens of positive alerts of active skimming fraud. Another preventive measure that can be taken is with CSG’s Smart Camera Analytics. These camera analytics provide real-time notifications with surveillance footage to detect loitering, vandalism, and fraud to determine if an ATM should be taken out of service.
Written By:
Alyssa Knapp
CSG Financial Technology Solutions Consultant
References:
Cook Solutions Group. (n.d.). Retrieved from ATM Fraud Deterrents: https://www.cooksolutionsgroup.com/security-solutions-new/atm-itm-skimming-attacks-deterrents
Krebs, B. (2016, May 5). KrebsonSecurity. Retrieved from Crooks Go Deep With ‘Deep Insert’ Skimmers : https://krebsonsecurity.com/2016/05/crooks-go-deep-with-deep-insert-skimmers/
Krebs, B. (2016, April 29). KrebsonSecurity. Retrieved from A Dramatic Rise in ATM Skimming Attacks: https://krebsonsecurity.com/2016/04/a-dramatic-rise-in-atm-skimming-attacks/
Lucas, P. (2023, August 7). Why Card Skimming, Already Bad, Is Getting Worse . Retrieved from Digital Transactions: https://www.digitaltransactions.net/why-card-skimming-already-bad-is-getting-worse/
NCR. (2022). Additional mitigation from Deep Insert Skimming. Retrieved from https://www.ncr.com/content/dam/web/documents/NCR_Brand_Datasheet_Internal_Skimmer_Prevention_Upgrade.pdf
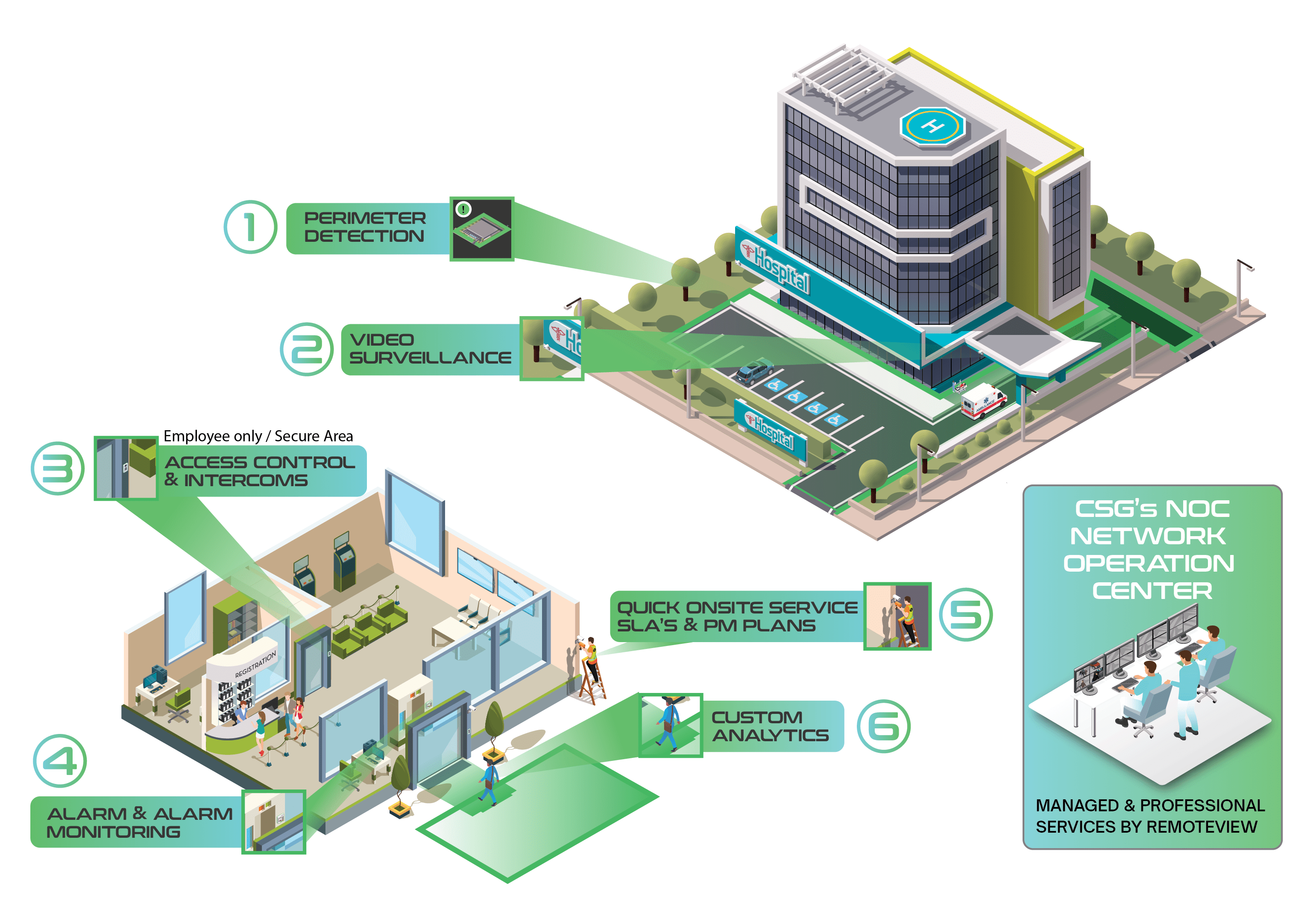
CSG's unique approach against multiple types of ATM fraud.
Our strategy extends beyond traditional surveillance, incorporating real-time monitoring, intelligent analytics, and proactive threat detection. Our approach is based on a layered security strategy that addresses various vulnerabilities, including:
- Hook & Chain, Physical Attacks: Fortify terminals against brute force attacks aiming to extract cash.
- Reg E Claims: Support compliance with Regulation E by providing evidence and transaction verification to resolve disputes.
- Software Vulnerabilities: Utilize AI based Endpoint Security to shield the ATM operating system from malware and other cyber threats.
- Data Compliance: Ensure the confidentiality and integrity of data stored on terminal hard drives using hard drive encryption.
- Card Skimming, Deep Insert and Cash Harvesting: Prevent unauthorized data capture and cash removal from terminals.
- Terminal Jackpotting: Guard against unauthorized software manipulation aiming to dispense cash fraudulently.
- Cash Dispensing and Cash Trapping: Secure dispensing mechanisms from tampering and unauthorized cash trapping devices.
- Transaction Reversal Fraud (TRF): Protect against manipulation techniques that reverse transactions to withdraw cash.
- Man-in-the-Middle (MITM) Attacks: By placing a device between the ATM and the Host, attackers pursue objectives such as interception, eavesdropping, modification, and impersonation.
The whitepaper delves into the emerging threat of deep insert skimming, a sophisticated form of ATM fraud characterized by wafer-thin devices hidden inside card readers, making detection challenging. These devices, found on ATMs globally, covertly collect magnetic stripe track 2 data, requiring criminals to also obtain the PIN through hidden cameras. The low profile of deep insert skimmers poses a unique challenge, evading traditional anti-skimming measures. The paper emphasizes proactive steps to protect machines, such as denying magnetic transactions, implementing PIN pad covers, and adopting comprehensive solutions like Cook Solutions Group's Suspicious Activity Notification and Smart Camera Analytics. These measures aim to enhance security, prevent skimming, and safeguard cardholder information.