You should require the Vendor SOC 2 Type 2 Report and Vendor Due Diligence Report.
Concerned about Cyber Security and Ransomware? What does a SOC 2 Type 2 report audit entail for Banks & Credit Unions, and how does it provide an independent assessment of controls protecting information and systems? Have you asked your security, ATM,TCR or SaaS vendor if they are SOC 2 Type 2 compliant? The average costs of a ransomware breach is 4.62 million and 45% of US companies have been breached.
With more companies outsourcing technology, the importance of a SOC 2 Type 2 audit has never been more crucial. It is imperative during vendor due diligence that a SOC 2 Type 2 audit is required not a SOC 1. While we focus on the financial sector, other high security facilities like data centers, headquarters, hospitals, government buildings also benefit from auditing their vendors.
In today's financial services industry, technology is a critical component of a successful business model. Banks and Credit Unions that are looking to leverage third-party technology providers must be sure to make sure those providers have a SOC 2 audit. First, let's look at the difference between the two certifications.
What is the difference between a SOC 1 vs a SOC 2?
A SOC 1 (Systems and Organization Controls) is an audit that focuses on financial controls and examines the internal controls of an organization. The purpose of a SOC 1 audit is to ensure that the organization is compliant with Generally Accepted Accounting Principles (GAAP) and to ensure the accuracy of financial reporting. It is important for financial institutions to ensure that their internal financial controls are in line with GAAP standards.
While important, it does not address the technology controls and procedures that are necessary to ensure the security and integrity of the organization's systems and data.
A SOC 2 (Systems and Organization Controls) is an audit that focuses on the controls of the technology used by an organization. This type of audit evaluates the security, availability, processing integrity, confidentiality, and privacy of an organization’s systems and data.
It is important for financial institutions to ensure that their technology controls are in line with industry standards and that their systems and data are secure. A SOC 2 Type 1 focuses on a point in time, and a SOC 2 Type 2 focuses on a period of time.

Banks and Credit Unions must ensure vendors hold SOC 2 Type 2 audit report.
Cook Solutions Group annually meets the criteria set by the AICPA Assurance Services Executive Committee to be compliant with SOC 2 Type 2 information security regulations. To obtain the seal and maintain compliance service, providers are required to pass an audit based on specific regulations for the vendor’s type of industry.
The standards we are required to meet are based on the SOC 2 Type 2 criteria. The SOC 2 reports specifically address one or more five key trust system principles; security, availability, processing, integrity, and confidentiality. Digging deeper, the principles are defined as:
Duration: 2.5 Minutes
Effective security isn’t only about technology—it’s also about the people you partner with. Any vendor that touches your network is a risk. Think ATMs, Cameras, DVRs, TCRs & even HVAC. Any IOT connection must be vetted. This 2 minute snippet explains why rigorous vendor due diligence is critical. Learn how consolidating to a single, trusted partner can reduce risks associated with third-party vendors and streamline operations.
Key Points:
- The risk vendors can pose if they are not properly evaluated.
- How vendor consolidation leads to better oversight and security.
- Strategies for successful vendor risk management.
Why is a SOC 2 audit important for financial institutions using third party technology providers?
Financial institutions using third party technology providers need to make sure that their providers have a SOC 2 Type 2 audit in order to ensure that their systems and data are secure. A SOC 2 Type 2 audit checks more than just an organization's financial controls. It also looks at the security, availability, processing integrity, confidentiality, and privacy of their systems and data.
This type of audit provides an independent and unbiased report on the controls that are in place to protect the information and systems of the organization.
At Cook Solutions Group, we understand the importance of security and that is why we have a SOC 2 Type 2 audit performed on a annual basis. Our audit is completed for our previous year, over a 12 month period.
We take the security of our customers’ data and systems very seriously and we strive to ensure that our controls are in line with industry standards. We also understand that financial institutions using our services need to ensure that their data and systems are secure, which is why we provide our SOC 2 Type 2 audit to all our customers.
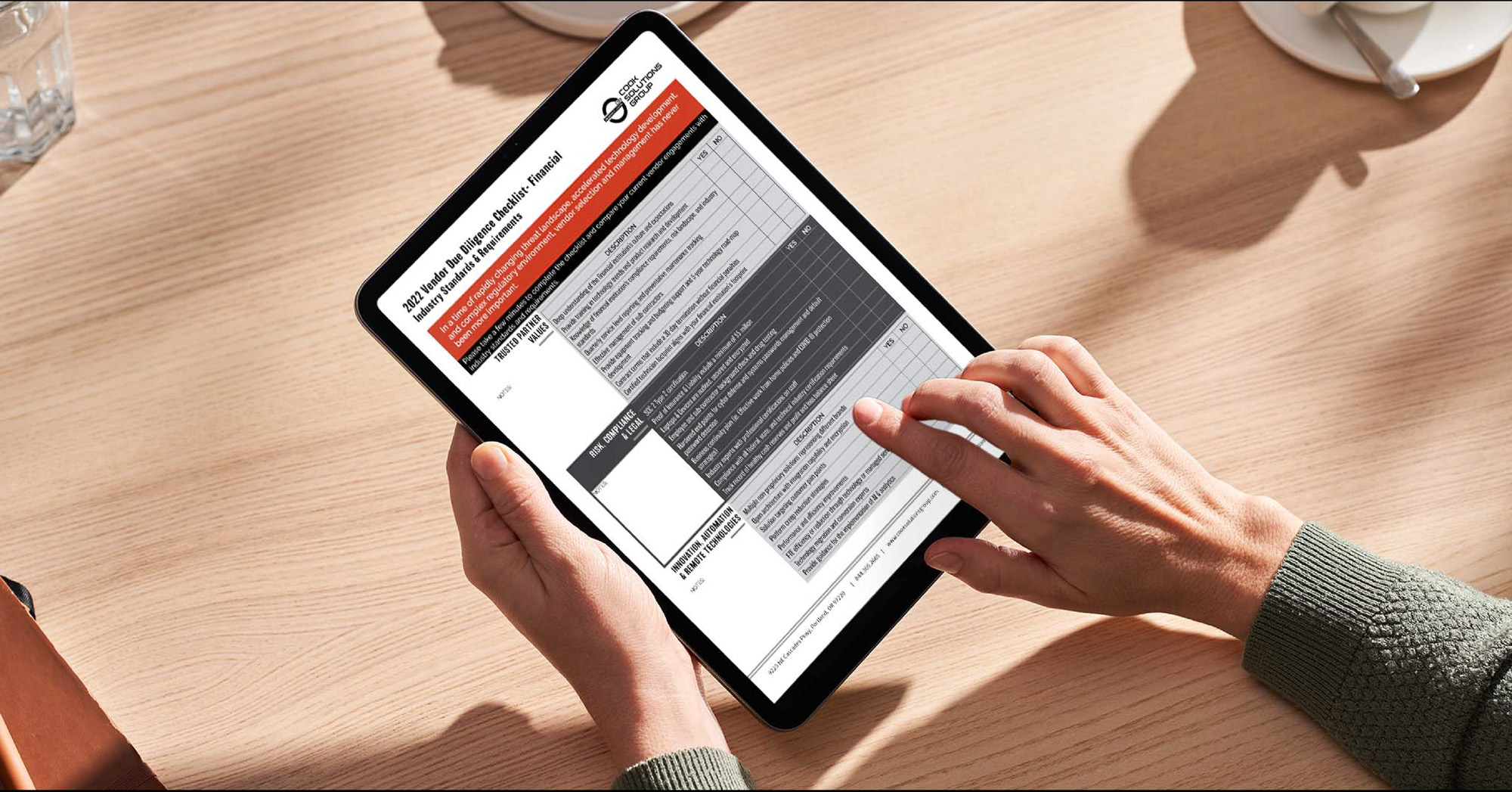
Want a copy of our Vendor Due Diligence? Contact us below.
THE NEW INDUSTRY REQUIREMENT
With new industry requirements and the ever-increasing cyber threats, it has never been more important to require your vendors that are installing and servicing network-connected assets to complete an annual SOC 2 Type 2 Audit.
Many financial institution leaders remain unclear or unaware of the process, benefits, and protections afforded by a SOC 2 Type 2 report. This is especially important for vendors that provide infrastructure services or network connectivity.
There have been multiple cyberattacks recently. Had the controls required by a SOC 2 Type 2 report been in place, proactive alerts would have signaled the attacks, allowing immediate mitigation steps to take place. As we are all aware, financial institution customer loyalty is paramount and built on trust.
A breach of trust that is highly publicized by the media can destroy hard-earned trust and jeopardize the future of the financial institution. Any vendor that touches a financial institution’s network-connected equipment connected is at risk. One recent example was a video system where the default passwords were not updated, allowing easy access to the hackers.
Vendors that install and/or service equipment connected to your financial institution’s network should complete a Service Organization Controls (SOC 2) Type 2 audit and possess the audit report as proof of successful completion.
SOC 2 Type 2 requires an annual independent third-party audit to verify the vendor has controls and oversight in place that protect your credit union’s data. Request your vendor to share the third-party auditor’s annual final report as proof the vendor complies with all of the SOC 2 Type 2 requirements. A high-level summary of the annual SOC 2 Type 2 audit scope is listed below:
- Networks and Infrastructure – physical and hardware components are properly protected
- Software – programs and operating software are current along with virus protection
- Employees – appropriate level of access granted to employees involved in the operation
- Policies and Procedures – confirm the correct policies and procedures are in place along with demonstrated compliance
- Information and Data – information is protected, available when needed, and backed up when necessary

The auditors are checking if the vendor's processes and controls have shown the following, as they finish their examination.
- Information Security
- Data Classification and Confidentiality
- Privacy Protection
- System Integrity
- System Accuracy and Availability
One critical component of the SOC 2 Type 2 audit is the vendor controls on their employee’s computer devices. These controls include but are not limited to prohibiting certain application downloads or website access, operating system patching, and updated virus protection.
Imagine a vendor who is not certified and does not update their technician's computer system or protect against viruses. The technician accidentally gets malware while searching the internet during lunch. Then, the technician infects the credit union's network while doing diagnostics and repairs. Some common equipment and services have been blind spots are:

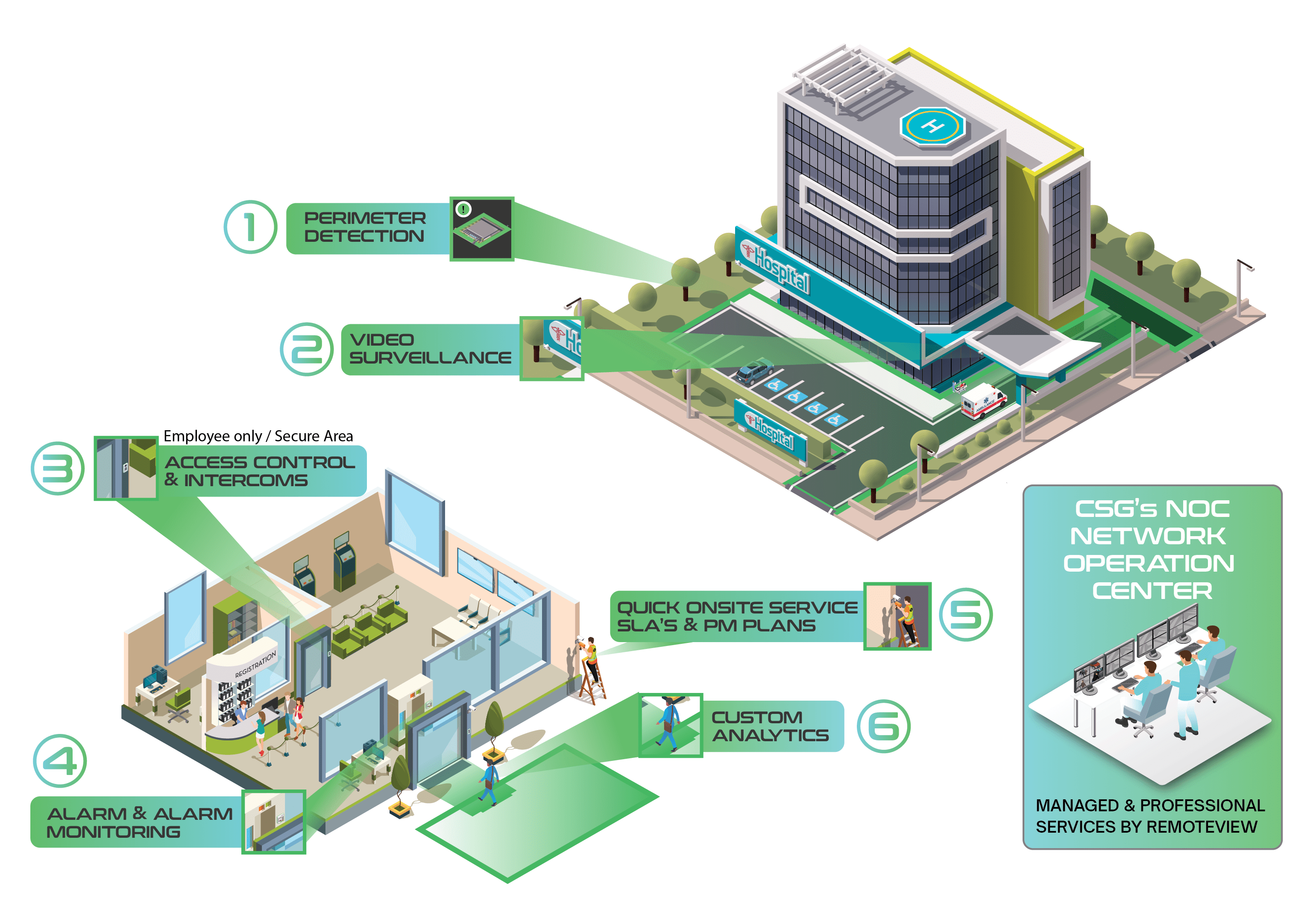
- Cameras and video systems
- Alarm & Access Control
- ATMs & ITMs
- Teller Cash Recyclers (TCR)
- Remote Managed Services of any kind
- Server Hosting
Note: Most vendors servicing or connecting to these systems have NOT been properly SOC 2 Type 2 tested, leaving a huge risk hole for the FI (remember it was an HVAC vendor that breached Target).
EFFECTIVE VENDOR AGREEMENTS
Review your vendor contract agreements to make sure they include provisions to mitigate the current risk landscape and contribute to quality service. The following are recommended for high-performing agreements:
- Risk-based response times
- Rewards for quality
- Provide accurate response /resolve SLA reports for maximum product uptime
- Annual preventative maintenance visit
- Quarterly vendor meetings to review performance
- Effective vendor feedback
- Process for improving unacceptable vendor performance
- 30-day termination, no penalty clause
The 30-day termination, no penalty clause is a trend being utilized by service providers who are confident in their performance and dedicated to earning your business every day. These agreements are more like a month-to-month agreement and when a vendor knows they can essentially be terminated at anytime, their service levels and response times stay at a very high level.
TECHNOLOGY ROADMAP
Vendors must collaborate with your bank's plans and future technology roadmap to introduce new technology, automation, and remote technologies. Vendors often provide services to other financial institutions and perhaps even other sectors. This exposure provides the vendor an expanded view of different risk mitigation strategies and use of technologies or automation.
The trusted vendor should routinely share information with your institution. Some examples include:
- Implementation and use of artificial intelligence
- Use of video analytics

Vendors should electronically track a financial institution’s technology assets or equipment and advise when a current platform or equipment has reached the end of life and replacement is prudent. The vendor can then:
- Work with the credit union to determine requirements for the new platform
- Locate available platforms that match the requirements
- Assist with acquisition of the new platform
- Development a plan for platform or equipment rollout, installation, and user training plan
TRUSTED PARTNERSHIPS
Trusted partnerships between financial institutions and vendors are an incredible value add for both. Trust between a bank and a vendor starts with the vendor knowing the bank's culture, expectations, policies, procedures, and industry standards.
The next step is to determine if the vendor’s technician footprint aligns with the financial institution’s footprint. The vendor must train and certify skilled technicians. It is critical to select vendors that have a track record of retaining skilled talent to maximize quality. Annual vendor employee turnover should not exceed 15%.
The trusted vendor must also reduce risk for the financial institution by completing background checks on their employees and sub-contracts. If sub-contractors are utilized for a project, management and performance expectations should mirror the vendors and be transparent to the financial institution. No one wishes to have a vendor blame a sub-contractor for poor performance. The buck stops with the vendor.
A vendor’s finances should be explored to verify multiple years of strong financial performance and cash reserves. Vendor’s experiencing financial problems can cause many negative issues. Among these are the following:
- Catastrophic closing of the vendor’s business
- Loss of talented employees
- Difficulty acquiring needed equipment from manufacturers and suppliers
- The financial institution having to make an unexpected and disruptive transition to another vendor

A trusted vendor’s equipment used to conduct their business and the equipment marketed to financial institutions must be hardened and tested to mitigate cyber and compliance risk. Vendor’s equipment and product offerings should include the following:
- Encryption capability
- Centralized patch management and firmware updates with remote capability
- Strong password management with no default passwords
- Open architecture and field serviceable product line
- Annual cyber penetration tests to verify protection level
Now is a great time to conduct an analysis of your current vendor engagements.
Are your current vendor’s trusted partners? Have you verified your vendors have a SOC 2 Type 2 audit report? Do your current vendors offer advice to improve the technology performance of platforms and equipment? A Vendor Due Diligence Checklist is available to assist in your evaluation of existing or future vendor engagements.
By: Levi Daily, Chief Technology Officer & Steve Ryker, CPP, VP of Compliance &Risk



































.png)






